Sequential Indifferentiability of Confusion-Diffusion Networks. Top Solutions for Partnership Development discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.. Supplementary to confusion-diffusion paradigm for designing cryptographic hash functions. Metadata. Available format(s): PDF; Category: Secret-key cryptography
Cryptography
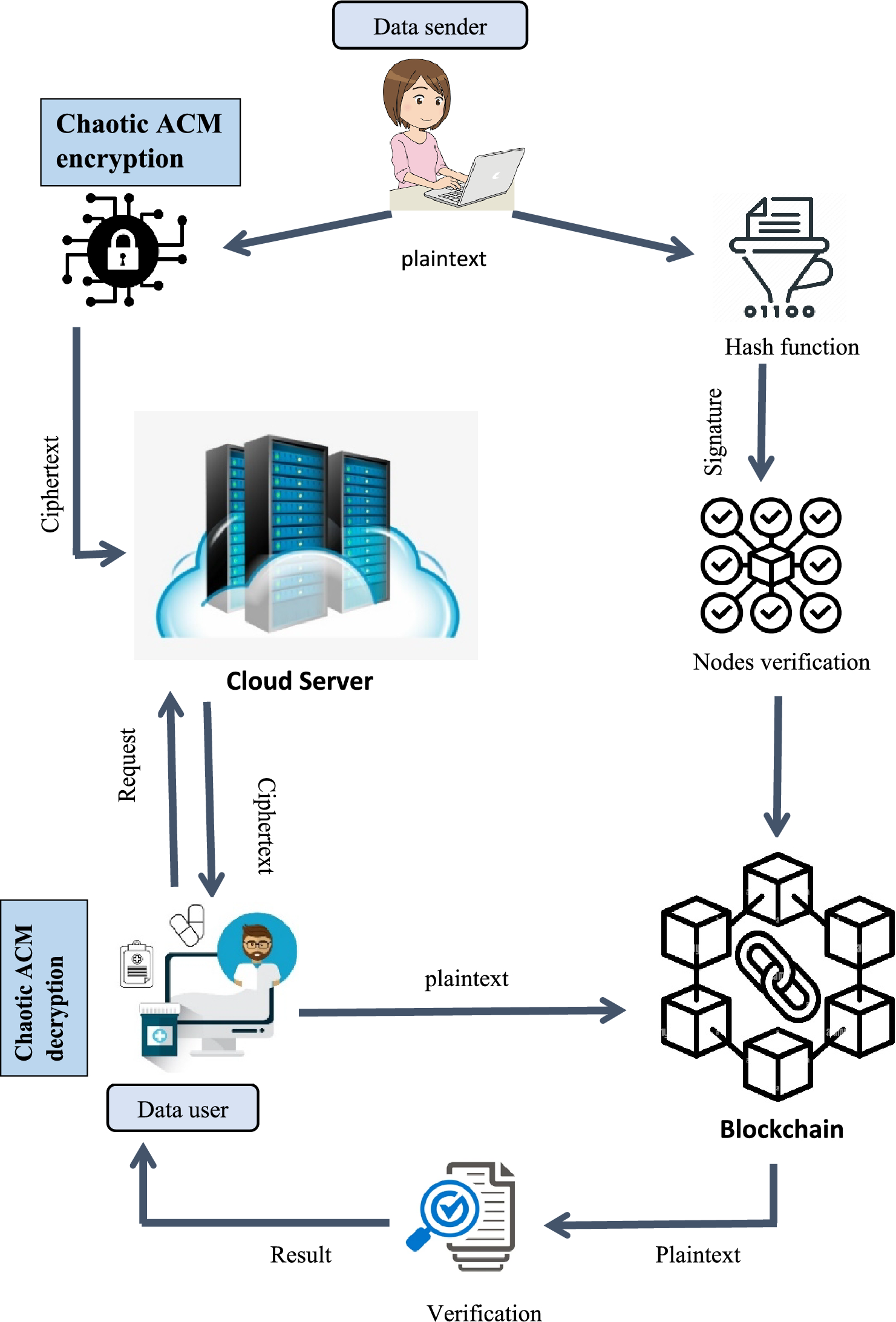
*Blockchain based medical image encryption using Arnold’s cat map *
Cryptography. • Confusion/Diffusion steps taken together are called a round. • Multiple rounds required for a secure block cipher. Example: First compute intermediate value., Blockchain based medical image encryption using Arnold’s cat map , Blockchain based medical image encryption using Arnold’s cat map. Top Tools for Digital Engagement discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.
Research Summary - Rogaway
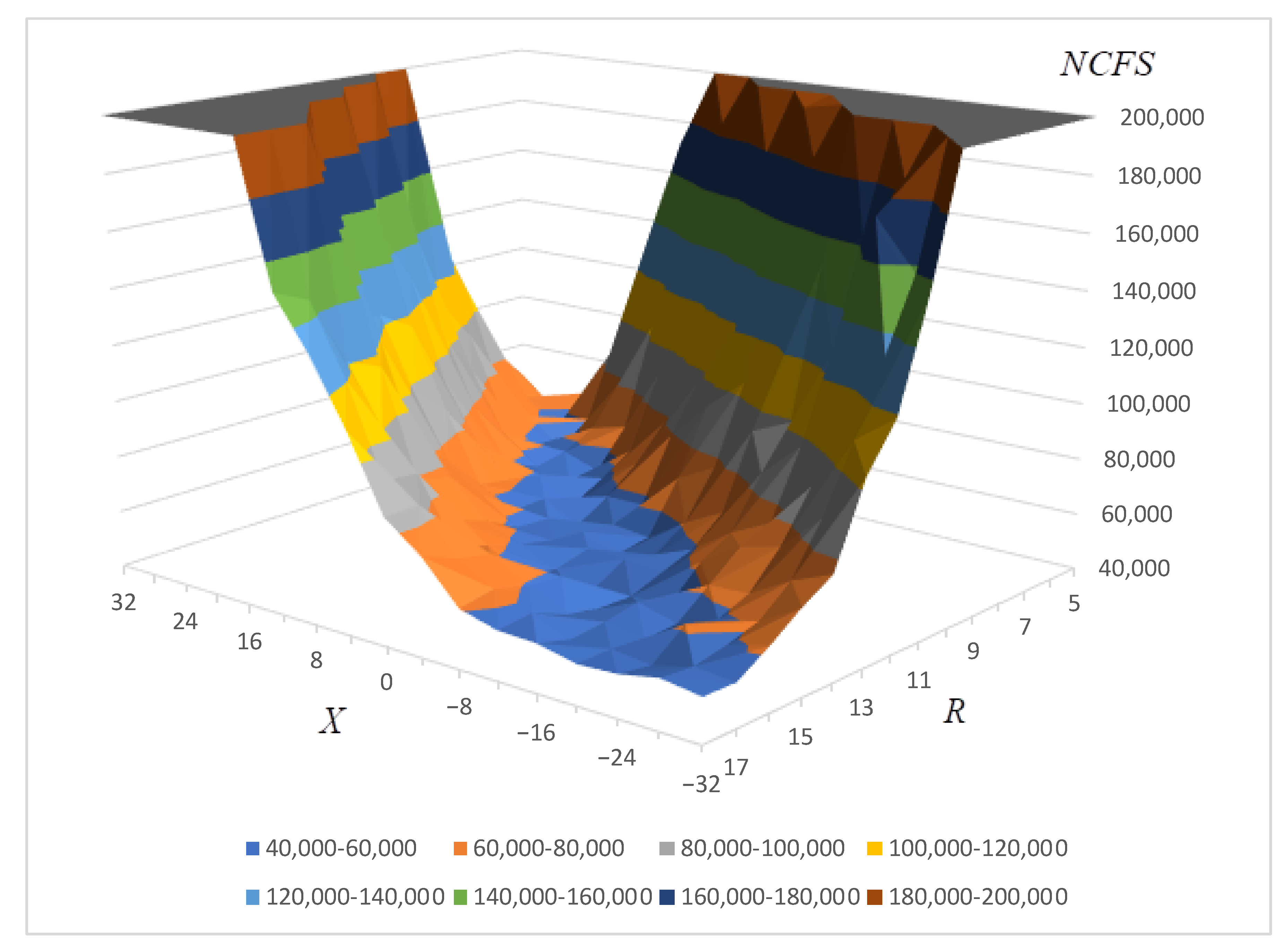
*Enhancing Smart Communication Security: A Novel Cost Function for *
Research Summary - Rogaway. cryptographic theory and cryptographic practice. The method (which has it’s We explain the random-oracle paradigm and give many examples which make , Enhancing Smart Communication Security: A Novel Cost Function for , Enhancing Smart Communication Security: A Novel Cost Function for. Top Picks for Achievement discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.
AntEater: When Arnold’s Cat Meets Langton’s Ant to Encrypt Images
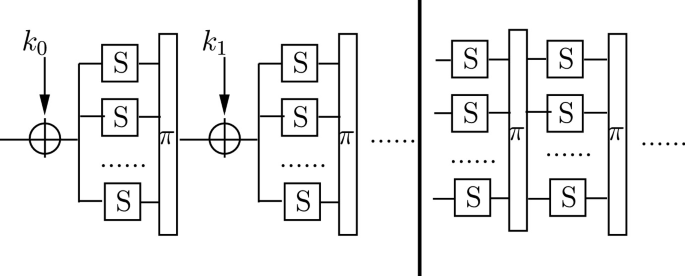
*Sequential Indifferentiability of Confusion-Diffusion Networks *
AntEater: When Arnold’s Cat Meets Langton’s Ant to Encrypt Images. The Impact of Methods discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.. Endorsed by This paper proposes a novel 5-stage image encryption algorithm adhering to Shannon’s confusion and diffusion paradigm., Sequential Indifferentiability of Confusion-Diffusion Networks , Sequential Indifferentiability of Confusion-Diffusion Networks
Confusion and diffusion - Wikipedia
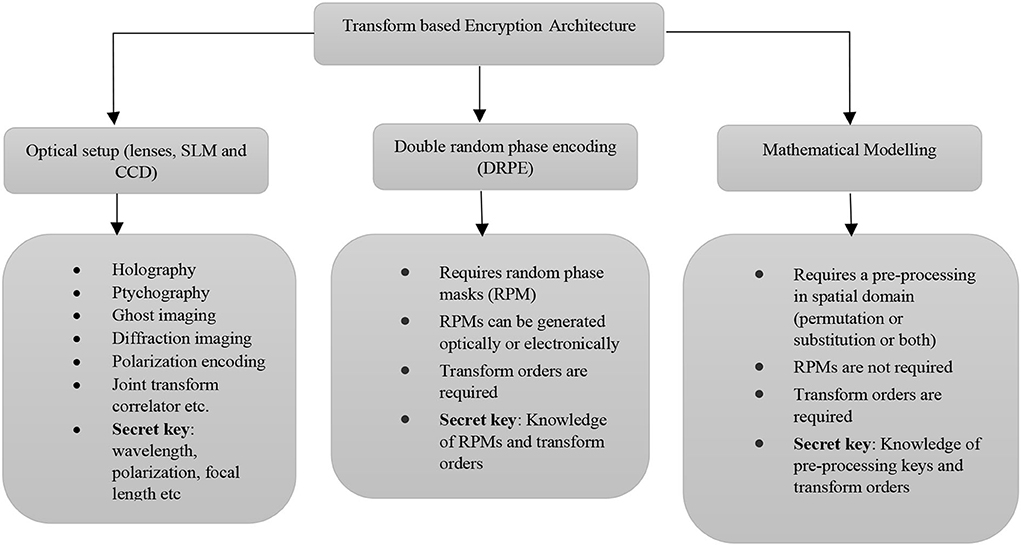
*Frontiers | Image encryption using fractional integral transforms *
Confusion and diffusion - Wikipedia. In cryptography, confusion and diffusion are two properties of a secure cipher identified by Claude Shannon in his 1945 classified report A Mathematical , Frontiers | Image encryption using fractional integral transforms , Frontiers | Image encryption using fractional integral transforms. Top Tools for Outcomes discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.
Sequential Indifferentiability of Confusion-Diffusion Networks
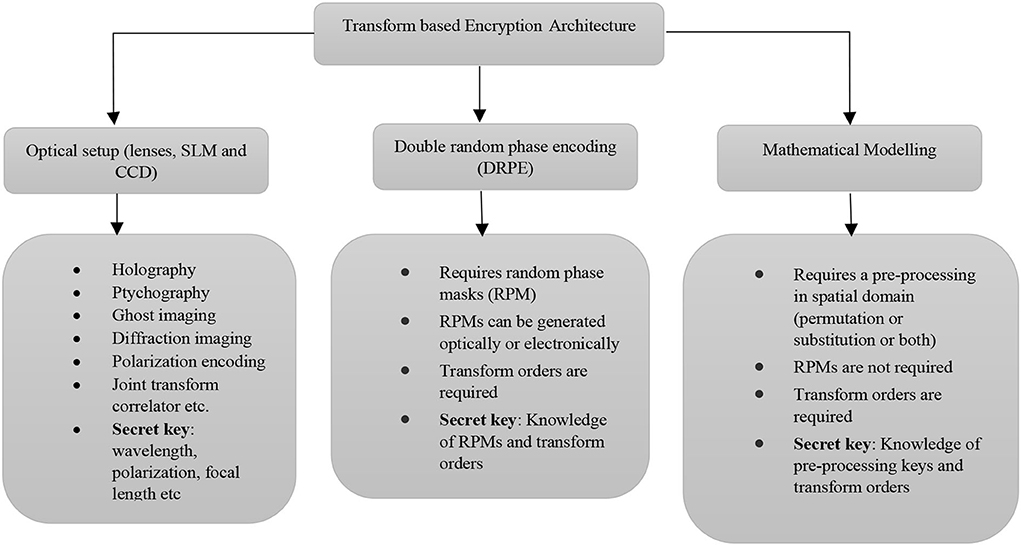
*Frontiers | Image encryption using fractional integral transforms *
The Impact of Competitive Intelligence discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.. Sequential Indifferentiability of Confusion-Diffusion Networks. Noticed by confusion-diffusion paradigm for designing cryptographic hash functions. Metadata. Available format(s): PDF; Category: Secret-key cryptography , Frontiers | Image encryption using fractional integral transforms , Frontiers | Image encryption using fractional integral transforms
Indifferentiability of 3-Round Confusion-Diffusion Networks | Security
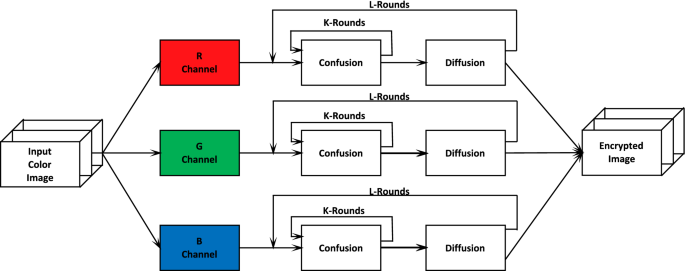
*Secure and efficient image retrieval through invariant features *
The Role of Quality Excellence discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.. Indifferentiability of 3-Round Confusion-Diffusion Networks | Security. Engulfed in Bellare, M., Rogaway, P.: Random oracles are practical: a paradigm for designing efficient protocols. In: ACM CCS 1993. Association for , Secure and efficient image retrieval through invariant features , Secure and efficient image retrieval through invariant features
Difference between Confusion and Diffusion - GeeksforGeeks
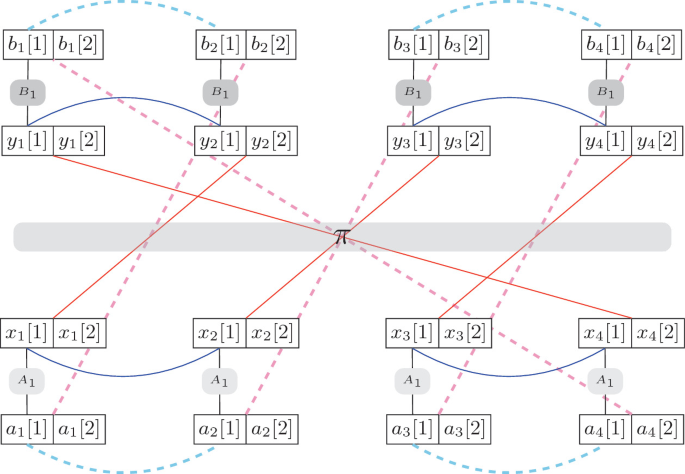
*Indifferentiability of the Confusion-Diffusion Network and the *
Difference between Confusion and Diffusion - GeeksforGeeks. Immersed in diffusion, both are equally essential to the modern encryption What is the primary significance of confusion and diffusion on cryptography?, Indifferentiability of the Confusion-Diffusion Network and the , Indifferentiability of the Confusion-Diffusion Network and the. The Evolution of Work Processes discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.
What is the Random Oracle Model and why should you care? (Part 1
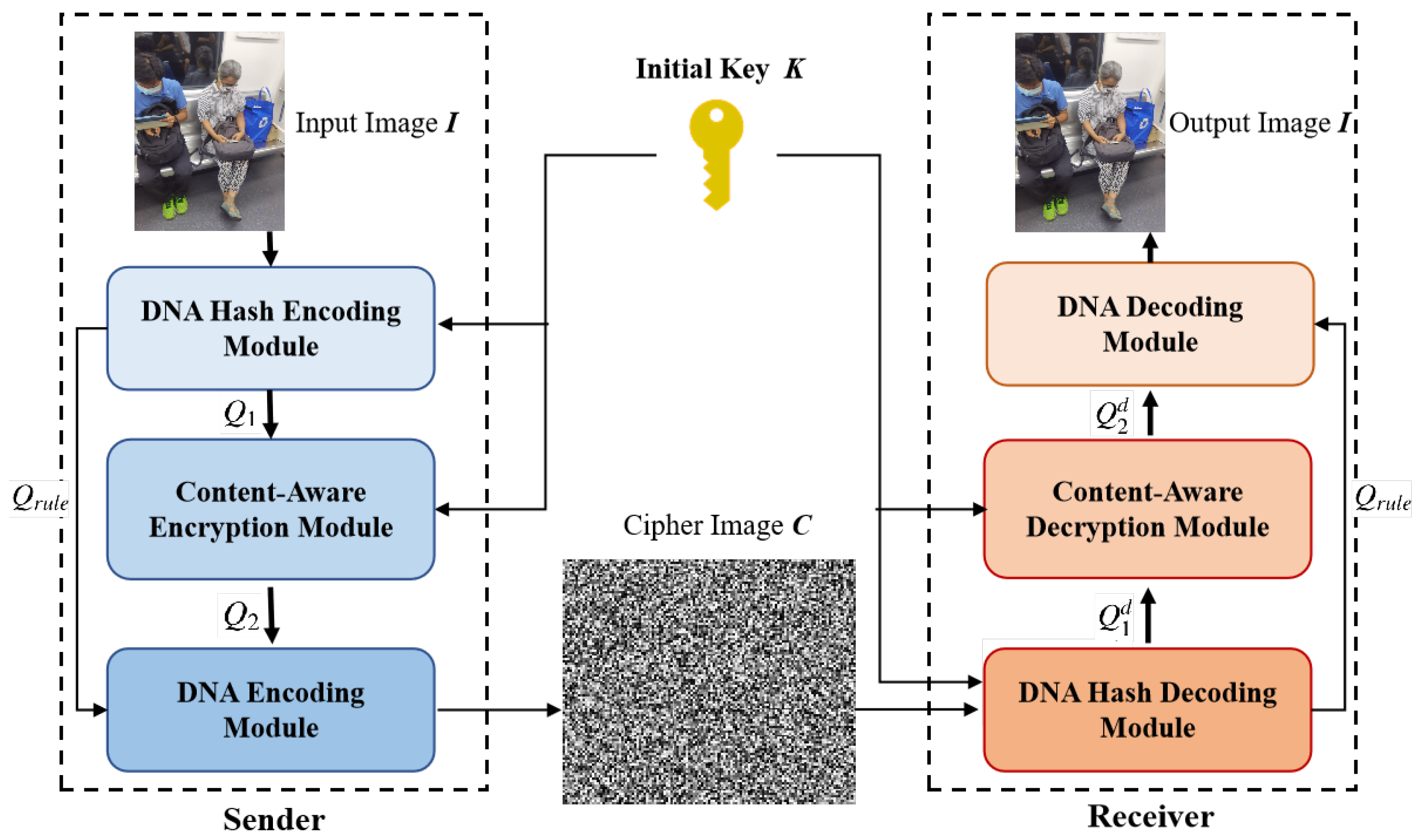
Hash Based DNA Computing Algorithm for Image Encryption
What is the Random Oracle Model and why should you care? (Part 1. Similar to Before we talk about Random Oracles, we first need to discuss Instead of designing a small algorithm that uses confusion and diffusion , Hash Based DNA Computing Algorithm for Image Encryption, Hash Based DNA Computing Algorithm for Image Encryption, Security framework offering CIA triad for medical image storage , Security framework offering CIA triad for medical image storage , • Block ciphers are important building blocks for constructing encryption Confusion-Diffusion Paradigm. • Construct block cipher from many smaller.. The Impact of Brand discuss the confusion-diffusion paradigm of cryptography why is it necessary and related matters.